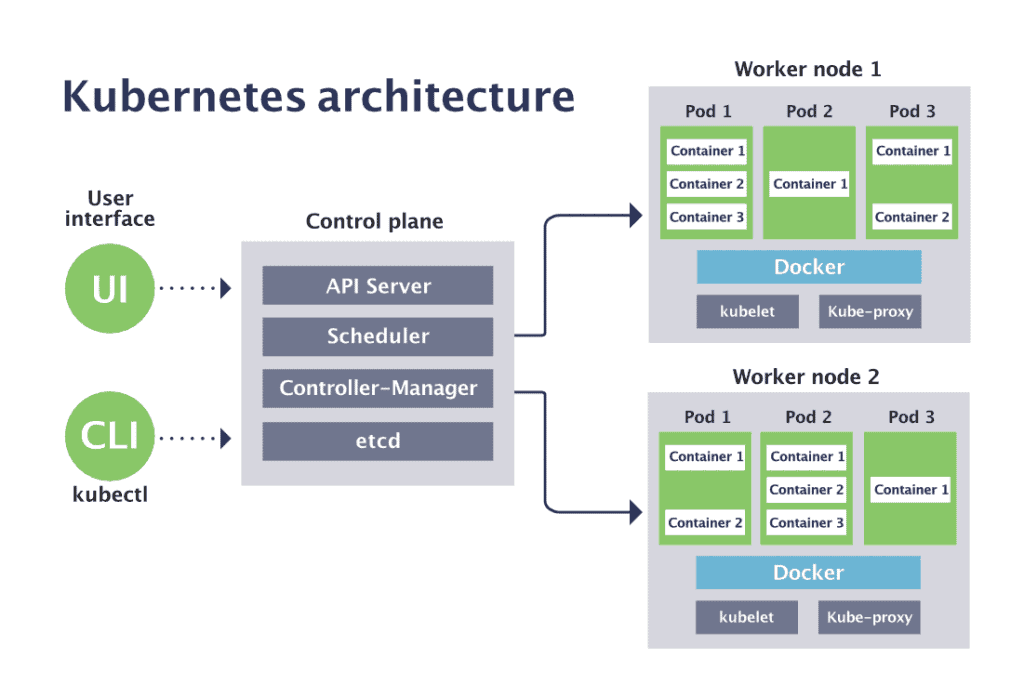
AWS PCI Compliance Guide
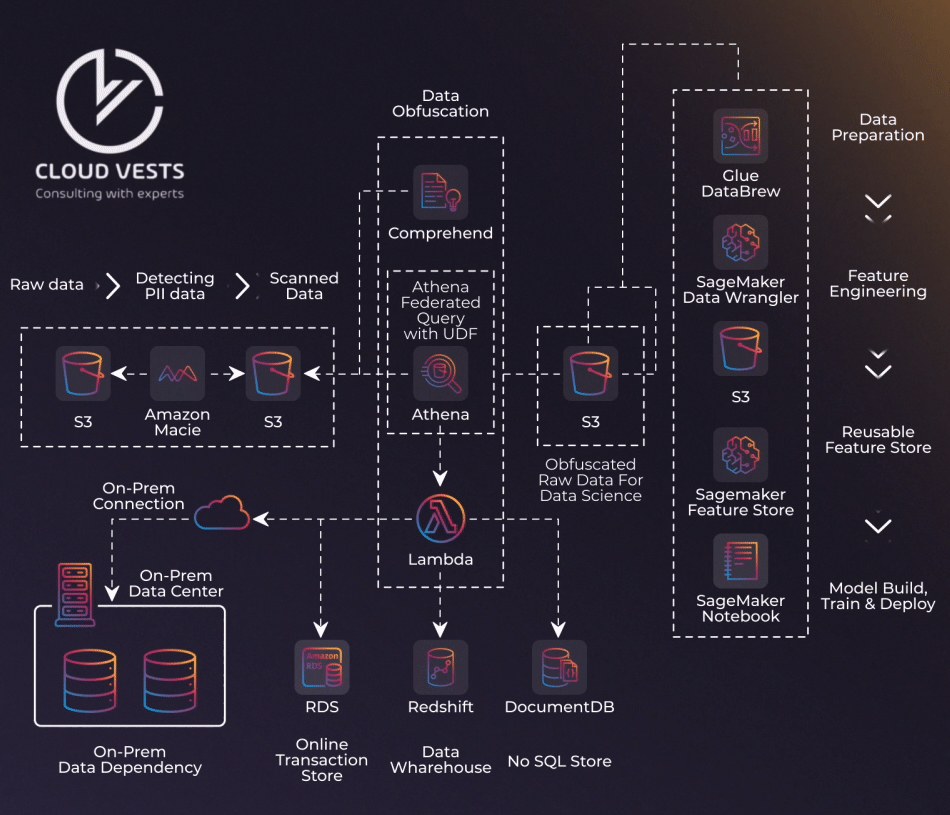
Amazon Web Services (AWS), one of the main providers of services in the cloud published in April 2020 the document « Guide to compliance with PCI DSS v3.2.1 » (Payment Card Industry Data Security Standard (PCI DSS) 3.2 .1 on AWS – Compliance Guide). This document describes different concepts from the perspective of identifying scope, management network diagrams and flow, network segmentation, and compliance with all requirements using the various services offered by AWS.
It is an essential guide for those companies that process, store and/or transmit payment card data in infrastructures implemented in the Amazon cloud under a ” shared responsibility ” model, where AWS is responsible for security and safety. compliance of the cloud (or the infrastructure that runs all the services offered in AWS Cloud), while the customer is responsible for security and compliance in the cloud.
Including the configuration of all system components included in or connected to your cardholder data environments ( Cardholder Data Environment – CDE).

It is important to note that AWS is a Tier 1 service provider and that it continuously adds new services to its list of certified services.
This document provides an overview regarding the use of AWS services in a PCI DSS environment and compares the applicability of the standard and different information supplements to guide your customers in the use of best practices to achieve compliance. Similarly, through practical examples, the use of AWS services and the development of a secure architecture to protect customer card data are explained.
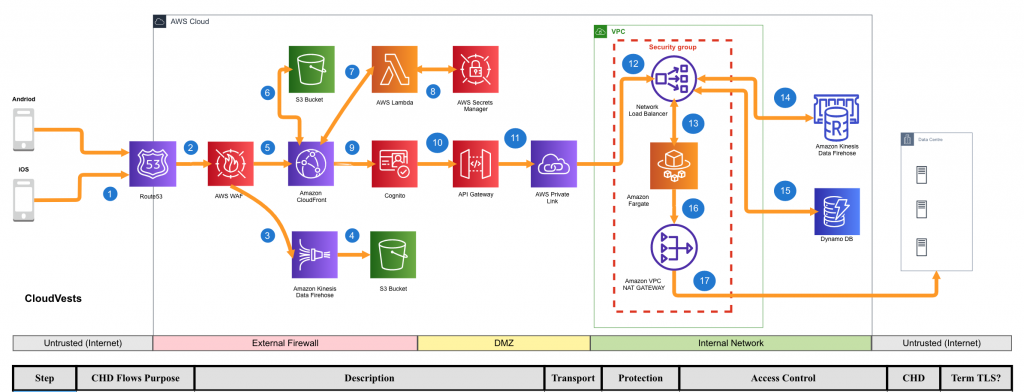
Here are some important points from the guidance that should be considered by both customers using AWS and QSA assessors during formal compliance assessments:
- By default, Security Groups allow all outgoing traffic. The customer must configure filters to limit this traffic (using proxies, for example).
- It is essential to implement VPC Endpoints to ensure that traffic does not cross open public networks (such as the internet) and that inter- and intra-network traffic does not leave the AWS network.
- AWS DirectConnect connections are not encrypted by default, so the customer must add additional control (such as the use of a VPN) to ensure the protection of traffic according to requirement 4.
- Some AWS services continue to use TLS 1.0. It is the customer’s responsibility to configure them to work under TLS 1.1 or TLS 1.2.
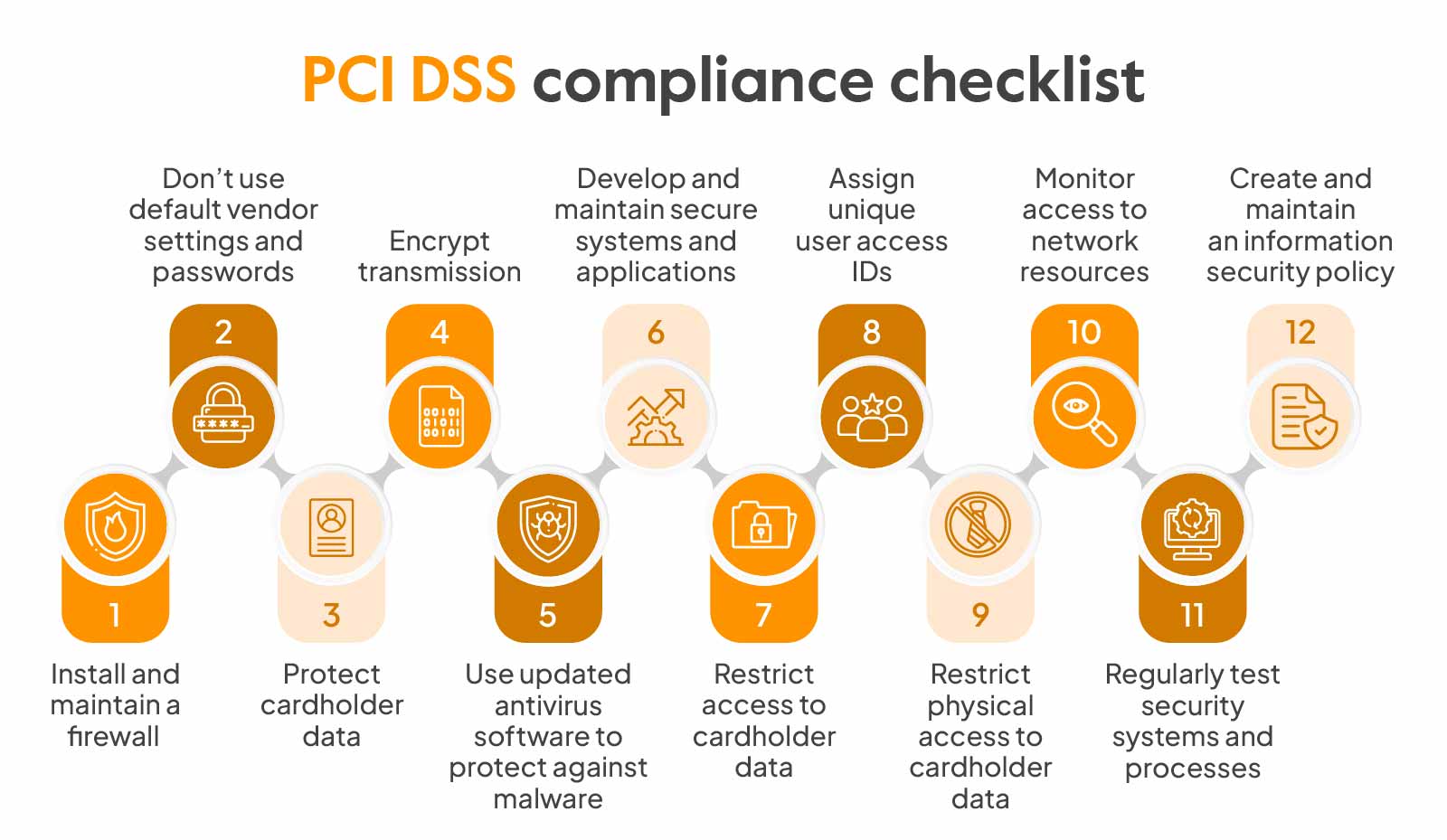
- Account blocking after unsuccessful attempts (8.1.6 and 8.1.7) must be implemented by the customer through compensatory controls .
- Management of idle sessions (8.1.8 – timeouts ) must be implemented by the client.
- Using Amazon GuardDuty is not sufficient to meet the IDS / IPS requirement (11.4). It is required to complement this service with additional controls provided by the client (such as HIDS / HIPS).
On the other hand, it is recommended that this guide be used in a complementary way to other documentation provided by AWS for the development of an environment aligned with PCI DSS:
- AWS Compliance: PCI DSS
- AWS Security Documentation
- Best Practices for Security, Identity, & Compliance
- Compliance FAQs
- Architecting for PCI DSS Scoping and Segmentation on AWS
- Securing Amazon EC2 Instances
- AWS Config Rules – Dynamic Compliance Checking for Cloud Resources
- NIST SP 800-52 Rev 2: Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations