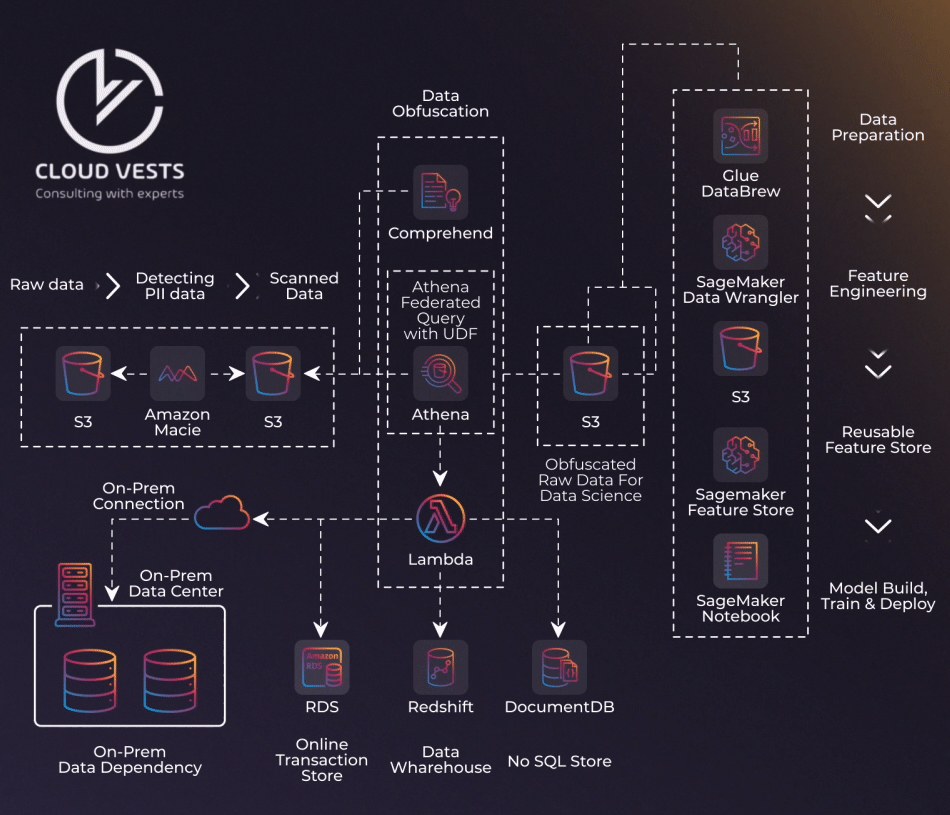
Kubernetes is an open-source container orchestration platform designed to run distributed applications and services at scale.
A K8s or Kubernetes cluster contains multiple components that are part of the Kubernetes control plane or Kubernetes nodes. Over the years, Kubernetes has become the hot topic in the DevOps space and is among the most sought-after platforms by developers. Since they are widely adopted to support various use cases, cluster security is becoming a major concern for many organizations. The growing adoption of the platform has caused attackers to target and abuse different parts of the cluster. Since Kubernetes is not immune to potential threats, such as misconfiguration
$ 4.3 billion – The projected market for application technologies in 2022, according to 451 Research . That’s more than double the $ 2.126 billion the company has forecast to be spent in 2019, and it also represents a 30% compound annual growth rate from 2017 to 2022.
Keeping the Kubernetes control plane and node components secure is vital, especially when you deploy it for compliance or business-related reasons.
With that said, in this post, we will discuss some of the critical steps to secure your Kubernetes deployments.
Let’s jump straight to that.
Fundamentals of a Kubernetes design
There are three main aspects to a strong Kubernetes network policy. That is, a Kubernetes cluster must be:
- Scalable – The cluster should be customizable and should not exclusively favor a single vendor.
- Easy to use – Design your cluster to work with a few simple commands.
- Secure – The cluster must follow the latest pod security policies and best practices.
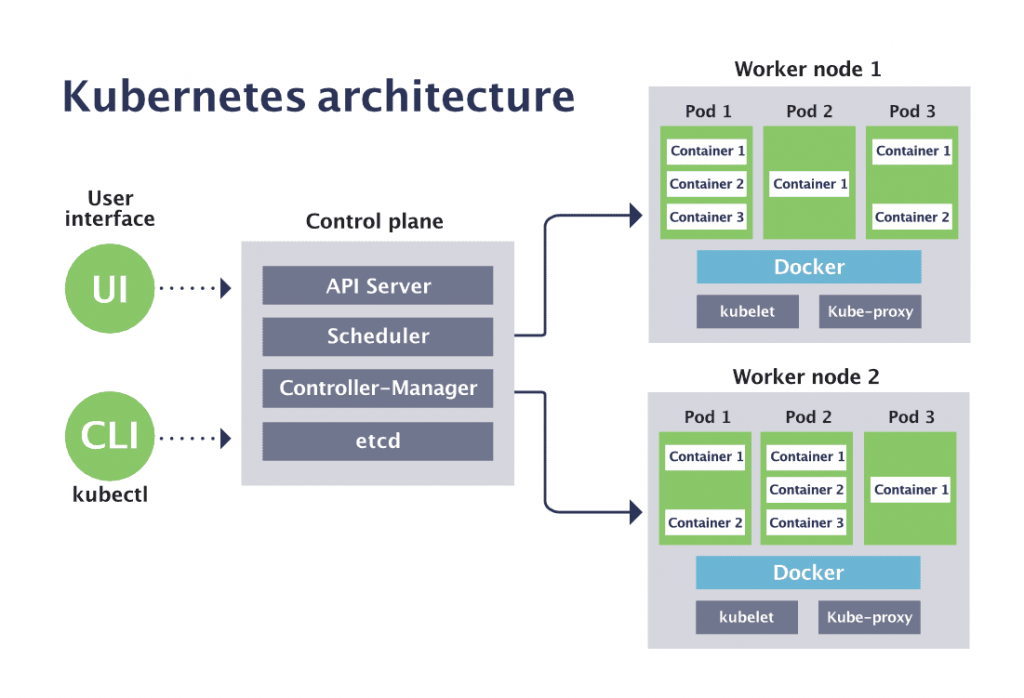
The control plane is responsible for controlling the cluster. Acting as the nerve center of a Kubernetes cluster, the control plane manages cluster health and configuration data. The control plane components ensure that your containers run in adequate numbers along with all the necessary resources.
However, the control plane is very susceptible to abuse by attackers because it is not easy to configure. While many companies configure their clusters to run in a certain way, some loopholes allow attackers to compromise the control plane.
To protect your Kubernetes control plane, check the following components and make sure to perform the listed operations.
etcd
Configuration of information and data about the state of the cluster. It is a key-value store database designed to be fault-tolerant and distributed to be the source of the truth about your cluster. To check if it is safe, type the following command:
Then modify the pod specification file etcd located at /etc/kubernetes/manifests/etcd.yaml
Finally, run the following command to check if encryption is already enabled:
-encryption-provider-configkube-controller-manageris responsible for running the cluster and controlling its functions. Ensures the correct number of pods are running at all times. In the event of a capsule being dropped, the controller immediately notices it and takes the necessary action.
To check if it kube-controller-manageris configured safely, first run the following command on your head node:
In the output, check and modify the following arguments:
kube-scheduler
Kube-scheduler takes care of the health of the cluster. Determine if your cluster needs new containers and provision them accordingly, ensuring that it meets the resource needs of your pod at all times. kube-scheduler
To check if it kube-scheduleris securely configured, run the following command on your head node:
In the output, check and modify the following arguments as necessary:
kube-apiserver
The kube-apiserver is the front-end of the control plane that handles external and internal requests. kube-apiserver determines the validated requests and submits them for processing. Try pressing the from an external IP to see if it is secure. If kube-apiserver respond, it means that other machines can do the same as well unless you have restricted the API server to your IP. To ensure that kube-apiserver it is not public and is exposed to the world, limit access to your Kubernetes cluster on GKE through the master authorized network configuration by running the following commands:
gcloud container clusters create --enable-master-authorized-networks --master-authorized-networks=CIDR
ps -ef | grep kube-apiserverCorrect RBAC configuration goes a long way toward preventing your cluster from being compromised. With RBAC, you can restrict pods and users to the CRUD operations that they can perform within a cluster. It enables a granular view of the cluster components that a user or pod can access and can help limit the attack surface of your cluster.
You can enable RBAC on your Kubernetes cluster through kube-apiserverbooting with the mark: -authorization-mode=RBAC
A malicious user can easily disable RBAC. To see if RBAC is disabled, run this command:
ps -ef | grep kube-apiserverSecuring node components
If the control plane is considered the nerve center, the components of the node are the muscle of the Kubernetes group. These nodes are responsible for running and controlling all containers and pods in a cluster. While it is not necessary to have worker nodes, it is better to have at least one worker node running and controlling all containers and pods on the same node, as the control plane does things complex.
The main components of a node are the container runtime, the kubelet, and.
- The container runtime runs containers on your cluster.
- The
kubeletis a small agent tasked with making sure his nodes and containers are up and running. - The
kube-proxyKubernetes facilitates service networks, managing network communications inside and outside the cluster.
Container runtime
Each computes node in a Kubernetes cluster has a container runtime. Most Kubernetes applications use Docker as the container runtime, although Kubernetes supports other runtime engines such as containers and CRI-O. Configuring your container runtime securely comes down to following security best practice issues from the engine you are using. Configuring your engine as recommended by your vendor ensures that your Kubernetes containers are safe from attack.
Kubelet
The kubelet is an agent that runs on every node in your cluster, ensuring that all containers are running. It also takes care of making configuration changes whenever necessary. A misconfigured kubelet can open a back door for attackers to your cluster.
You can use a kubelet configuration file or use arguments in the running kubelet executable to configure your kubelet. You can find your kubelet configuration file by running the following command and looking for the --config argument:
ps -ef | grep kubelet | grep config
ps -ef | grep kubelet
- Set
--rotate-certificatesin. If you are using a kubelet configuration file, set itRotateKubeletServerCertificateto. If you’re not already doing so, make sure your kubelets get their certificates from the API server. - Establish
--tls-cert-fileand--tls-private-key-fileproperly. If you are using a kubelet configuration file, settlsCertFileandtlsPrivateKeyFileproperly so that all connections on the kubelets go through TLS.
it is a network proxy that runs on every node in your cluster and maintains the network rules on these nodes. It ensures that your nodes can communicate with internal and external resources as needed and allowed.
Securing comes down to ensuring the security and integrity of your kubeconfig file. To make sure your file is safe, first find the kubeconfigfile in use by running:
ps -ef | grep kube-proxyFrom the output, make sure the permissions are set to 644 or more stringent to help maintain the integrity of the file.
Then run the following command on each worker node using the same kube-proxy configuration file location:
In the output, set the permissions root:rootto prevent any unauthorized access to the file.
Last Words
Keeping the Kubernetes control plane and node components secure ultimately comes down to following the basics. While configuring each of the components of your cluster may seem overwhelming, doing so will ensure that you can protect your applications and deployments from unwanted threats and attacks. You can significantly reduce your attack surface and avoid common configuration errors by following these configuration recommendations.
For more information on Kubernetes best practices, read the Kubernetes Best Practices published by O’Reilly Media. You can sign up for free access to two full chapters of this book and learn more about building great applications on Kubernetes.